Task 1: Install ISE 2.4 VM. Access the VMware WorkStation / Esxi, and Power on the VM, Once you power on, you will see the ISE 2.4 Login Screen, Log IN with username Setup. Hence this is new VM so it will run installation wizard with localhost login:setup. Now follow the below figure to configure the ISE from basic. ISE 2.4 Intune integration. Device Posturing using Cisco ISE. Content for Community-Ad. Follow our Social Media Channels. ISE 2.4 Intune integration. Device Posturing using Cisco ISE. Content for Community-Ad. Follow our Social Media Channels.
The purpose of this blog post is to document the configuration steps required to configure Wireless 802.1x authentication on a Cisco vWLC v8.3 using Cisco ISE 2.4 as the RADIUS server.
WLC Configuration
Define AAA Servers
- Login to the WLC WebGUI
- Click Advanced
- Navigate to Security > AAA > RADIUS > Authentication
- Click New
- Define the IP address of the RADIUS Server (ISE)
- Define the Shared Secret
- Ensure Support for CoA is Enabled
- Click Apply
- Navigate to Security > AAA > RADIUS > Accounting
- Click New
- Define the IP address of the RADIUS Server (ISE)
- Define the Shared Secret
- Click Apply
Create WLAN
- Navigate to WLANs > WLANSs > WLANs
- Select Create New and click Go
- Define a Profile Name e.g. LAB_WLAN
- Define a SSID e.g. LAB_SSID
- Define an ID e.g. 1
- Click Apply
- Under the General tab, ensure the Status is Enabled and Security Policies is [WPA2][Auth (802.1x)]
- Under the Security tab, select AAA Servers
- Ensure the Auth Called Station ID Type is AP MAC Address:SSID
- From the drop down list select the previously defined Authentication and Accounting Servers
- Ensure Interim Update is selected
- Scroll down and remove LOCAL and LDAP, ensure only RADIUS is used for authentication
- Under the Advanced tab, tick the box for DHCP Addr. Assignment
- Under the Radius Client Profiling section, tick the box for DHCP Profiling and HTTP Profiling
- Click Apply
AP Groups
- Navigate to WLANs > Advanced > AP Groups
- Click Add Group
- Define a name for the group, e.g. LAB_GROUP
- Click Add
- Click the newly created AP Group
- Define a NAS-ID e.g vWLC
- Click Apply
- Click WLANs tab
- Click Add New
- Select the WLAN SSID from the drop down list, click Add
- Click the APs tab
- Select the AP(s) to add to the Group, click Add APs
NOTE – the AP(s) will now be reconfigured and rebooted
- Click <Back when complete
ISE Configuration
Authentication Policy
- Create or modify the Authentication Policy
- Create a rule to authenticate using PEAP/MSCHAPv2, named appropriately
Rule Name:-
MSCHAPv2
Conditions:-
Network Access-EapAuthentication EQUALS EAP-MSCHAPv2
Wired_802.1x
Use:-
Authorization Policy
- Create new Authorization Rules as per the table below
| Rule Name | Conditions | Profiles |
| Domain Admins | Radius Called-Station-ID MATCHES .*(:)$ LAB_AD-ExternalGroups EQUALS lab.local/Users/Domain Admins Wireless_802.1X | PermitAccess |
| Domain Users | Airespace Airespace-Wlan-Id EQUALS 1 LAB_AD-ExternalGroups EQUALS lab.local/Users/Domain Users Wireless_802.1X | PermitAccess |
| Domain Computers | LAB_AD-ExternalGroups EQUALS lab.local/Users/Domain Computers Wireless_802.1X | PermitAccess |
| Default | PermitAccess |
When the user connects the AP MAC Address + SSID is sent in the radius packet, this can be used in the Authorization rule to distinguish users from the SSID they are connecting from. The first rule for Domain Admins uses the Called-Station-ID radius attribute with a regex to match the SSID the user is connected to.
In addition to using the Called-Station-ID radius attribute to determine the SSID the user is connected to, if the WLC/AP is Cisco we can use the attribute Airespace-Wlan-Id. For members of the Domain Users group we will use this value. It is important to note the value specified must equal the number of the SSID defined in the WLC SSID configuration.
For Domain Computers we will not require the computer can authenticate from a specific WLAN SSID, just that it is a member of the Domain Computers AD group.
Verification and Testing
With a wireless enabled device login as a user that is a member of the AD group Domain Users. From the ISE logs we can determine the user was matched against the correct Authorization rule and the conditions worked.
Logoff and login as a user that is a member of the AD group Domain Admins. From the ISE logs we can determine the user was matched against the correct Authorization rule and these conditions also worked.
From the detailed output we can determine the AD Group, the NAS-Identifier defined in the AP Group configuration and the Called-Station-ID.
From the WLC we can navigate to Monitor > Clients and determine the client properties. We can determine user2 associated to the correct SSID and used 802.1x authentication, with PEAP as the protocol.
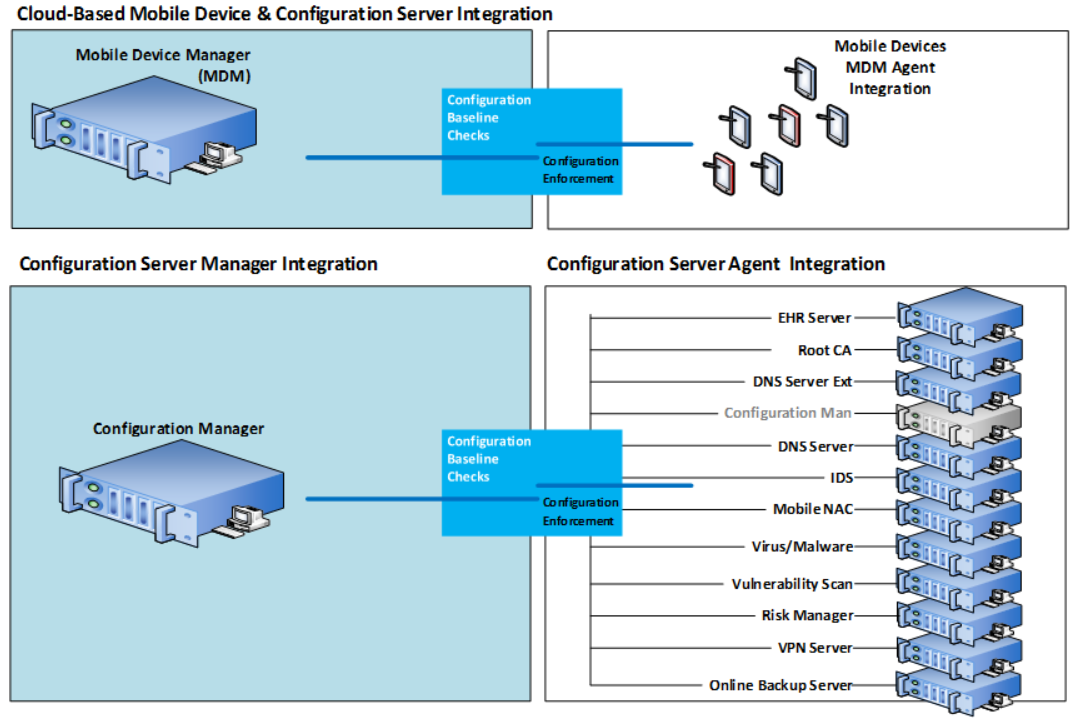
-->Intune integrates with network access control (NAC) partners to help organizations secure corporate data when devices try to access on-premises resources. If the device is enrolled in Intune and is compliant with Intune device compliance policies, the NAC solution allows the device to access corporate resources. For more information about how the NAC integration works, see Network access control (NAC) integration with Intune.
Cisco Identity Services Engine (ISE) integration with Microsoft Intune MDM Services uses Azure Active Directory (Azure AD) token-based authentication to access Intune services, and then uses that information to grant or deny network access to mobile devices.
Import the public certificate from the Intune tenant into ISE
Cisco Ise 2.1 Deployment Guide
Sign in to the Azure portal.
Use the browser to get the certificate details. For example, in Microsoft Edge, select the HTTPS lock symbol, and then select Certificate. In the Certificate window, select the Certification Path tab.
In the local machine certificate store, find the Baltimore CyberTrust Root certificate, and then export the root certificate.
In ISE, select Administration > System > Certificates > Trusted Certificates, and then import the root certificate that you exported in step 3. Give the certificate a meaningful name, such as Azure MDM.

Export the Cisco ISE self-signed certificate

In the ISE console, select Administration > System > Certificates > System Certificates, select the Default self-signed server certificate, and then select Export.
Select Export Certificate Only (default), and then select a location to save it to.
Run the following PowerShell script on the exported certificate file: Ti cc2540 usb cdc serial port driver.
After the script runs, the values are stored in the variables. Type the variable name at the PowerShell prompt to review the values, as shown in the following example:
Keep the values for
$base64Thumbprint,$base64Value, and$keyid. They will be used in the Configure the application manifest and upload to Azure step.
Create an ISE application in Azure
In the Azure portal, select Azure Active Directory.
Under Manage, select App registrations, then select New registration.
Enter the following information for the application:
- Name: Enter a name for your application, such as Cisco ISE.
- Supported account types: Select an option to specify who can use the application.
- Redirect URI (optional): Select Web, and then enter the redirect URI for the location that the access token is sent to.
Select Register to complete the app registration.
Configure the application manifest and upload to Azure
After the registration is complete, the Azure portal displays the application's Overview page, which includes the Application (client) ID.
On the application Overview page, select Manifest under Manage.
Select Download to download the manifest file, and then save it as a JSON file. Do not change the name of the manifest file.
Update the keyCredentials field in the JSON file as shown in the following example:
- Replace Base64 Encoded String of ISE PAN cert with the exported, edited certificate file from ISE, which is the
$base64Valuevalue from the PowerShell script in Export the Cisco ISE self-signed certificate. - Replace
keyIdwith the$keyidvalue from the PowerShell script. - Replace
customKeyIdentifierwith the$base64Thumbprintvalue from the PowerShell script.
For more information about the KeyCredentials complex type, see KeyCredential Type.
- Replace Base64 Encoded String of ISE PAN cert with the exported, edited certificate file from ISE, which is the
Save the JSON file, and then select Upload to upload it to Azure.
Get the endpoints to configure Cisco ISE

In the Azure portal, select Azure Active Directory > App registrations > Endpoints.
Note the following endpoints:
- MICROSOFT AZURE AD GRAPH API ENDPOINT
- OAUTH 2.0 TOKEN ENDPOINT
Solidworks plugin for ansys. Also note the Application (client) ID of the ISE application.
These values are used when you configure the Microsoft Intune server in ISE.
Configure API permissions
Cisco Ise 2.4 Ad Integration Problems
In the Azure portal, select Azure Active Directory > App registrations, and then select the ISE application.
Select API permissions > Add a permission.
Select Microsoft Graph from the APIs.
Select Delegated permissions, and then select the following permissions:
Permission Description Directory.Read.AllRead directory data User.ReadSign in and read user profile DeviceManagementConfiguration.Read.AllRead Microsoft Intune Device Configuration and Policies DeviceManagementServiceConfig.Read.AllRead Microsoft Intune configuration openidSign users in offline_accessMaintain access to data you have given it access to Select Application permissions, expand Directory, and then select the
Directory.Read.Allpermission.Select Intune from the APIs, select Application permissions, and then select the
get_device_compliancepermission.Select Add permissions.
Select Grant admin consent for <tenant> to grant administrator consent to the configured permissions. Select Yes when you are prompted to confirm the consent action.
Configure the Microsoft Intune server in ISE
Cisco Ise 2.4 Ad Integration Solutions
For more information about how to configure external MDM servers, see Define Mobile Device Management Servers in ISE.
Cisco Ise 2.4 Installation Guide
The following fields are important for Microsoft Intune:
Cisco Ise 2.4 Ad Integration System
- Auto Discovery URL: The endpoint at which an application can access directory data in your Microsoft Azure AD directory by using the Graph API. Enter the value of Microsoft Azure AD Graph API Endpoint from the Azure portal. The URL is in the form of
https://<hostname>/<tenant_ID>(for example,https://graph.windows.net/47f09275-5bc0-4807-8aae-f35cb0341329). An expanded version of this URL is also in the property file, which is in the form ofhttps://<Graph_API_Endpoint>/<TenantId_Or_Domain>/servicePrincipalsByAppId/<Microsoft Intune AppId>/serviceEndpoints?api-version=1.6&client-request-id=<Guid.NewGuid()>. - Client ID: The unique identifier for your application. Use this attribute if your application accesses data in another application, such as the Microsoft Azure AD Graph API, Microsoft Intune API, and so on.
- Token Issuing URL: The endpoint at which your application can obtain an access token by using OAuth 2.0. Enter the value of the Oauth 2.0 Token Endpoint from the Azure portal. After your application is authenticated, Azure AD issues an access token to your application (ISE). This token allows your application to call the Graph API or Intune API.
- Token Audience: The recipient resource that the token is intended for, which is a public, well-known APP ID URL to the Microsoft Intune API.
